If you’ve ever wondered what the dark web looks like, here’s your chance to find out. In fact, even if you’re not sure what the dark web is, this guide will help you understand it in no time.
After reading this guide, you’ll know why the dark web is such an attractive place for cybercriminals and how to best protect yourself from their scams, spam, phishing attacks, and other schemes.
What is the Dark Web?
First, let’s talk about what the dark web is not. The first thing that many people think of when they hear dark web is Silk Road and other black markets—that’s not what we mean by dark web.
The internet you use every day is actually a subset of what we call the surface web, which refers to anything searchable by a traditional search engine like Google or Bing. The surface web includes your email accounts, banking information and shopping sites—basically any content that can be found with a traditional search engine. It also represents a relatively small percentage of total internet traffic—less than 10%.
Everything else that isn’t accessible with a regular browser? That’s dark web.
Like it sounds, most dark web pages are hidden behind services like Tor; only those using special tools (called Tor browsers) can access them. To understand why someone would want to visit these hidden parts of the internet, it helps to know what they offer: anonymity and encryption.
Because dark web users are masked by Tor from third-party monitoring/tracking and almost completely untraceable via IP address or geographic location (since exit nodes may be in another country altogether), transactions can be both secure and anonymous for users—and thus ideal for illegal activities including buying drugs online.
But so much more exists on darknet beyond nefarious uses; good old Wikipedia was even hosted there at one point, but Facebook is still there.
What is Tor?
Tor, short for The Onion Router, is a specialized browser that allows users to browse websites anonymously. Originally developed by United States Naval Research Laboratory employees in an attempt to protect government communications online, Tor was released to the public for free in 2004 and has since become one of the most popular anonymous communication tools on Earth.

It’s typically used by people living under authoritarian regimes or anyone who wants unfettered access to information without being tracked—like some journalists and political activists.
However, it’s also a preferred tool of nefarious hackers who want anonymity while they trade goods and services illegally on dark web marketplaces like AlphaBay or Hansa Market.
How Does Tor Work?
When you use Tor, your internet traffic gets routed through several relays before reaching its destination. Each relay knows only what information to pass along to the next hop until your IP address reaches its final destination.
That way no one—not even those running servers where you surfed from or are surfing toward—can see what sites you’re accessing or how much time you spend there.
Because of its encrypted nature, only trusted exit nodes can actually read any data transmitted over Tor; malicious exit nodes cannot do so as part of their job description with regard to TLS/SSL data encryption and will be booted out of relays if discovered violating protocol rules about not reading data sent over untrusted connections.
What Can I Find on Dark Web?
Well, it’s really a fancy question for anyone who already saw some kind of darkness there, and it’s really difficult to answer, because there is too much scam and phishing sites.
But let’s take a look with few examples.
-* Note: We will not disclose names or URLs of these forums or websites for your own safety.

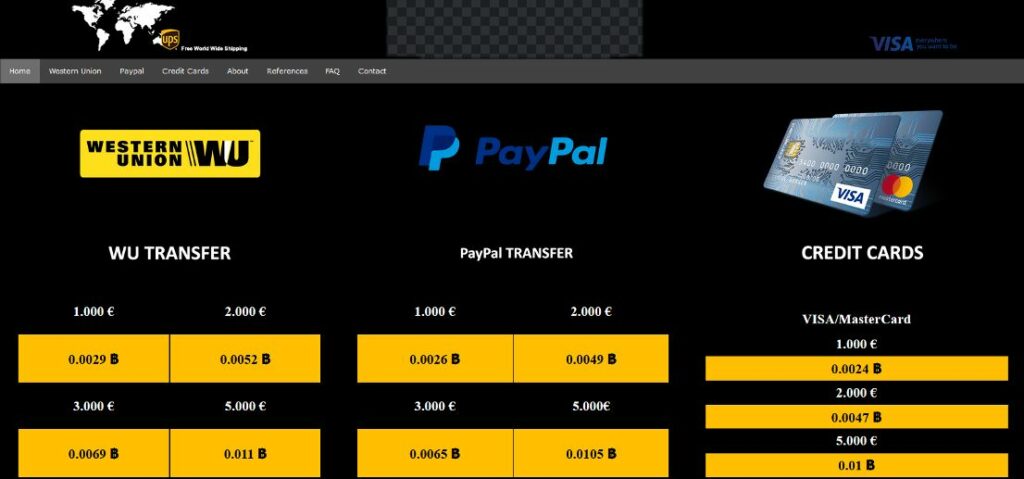
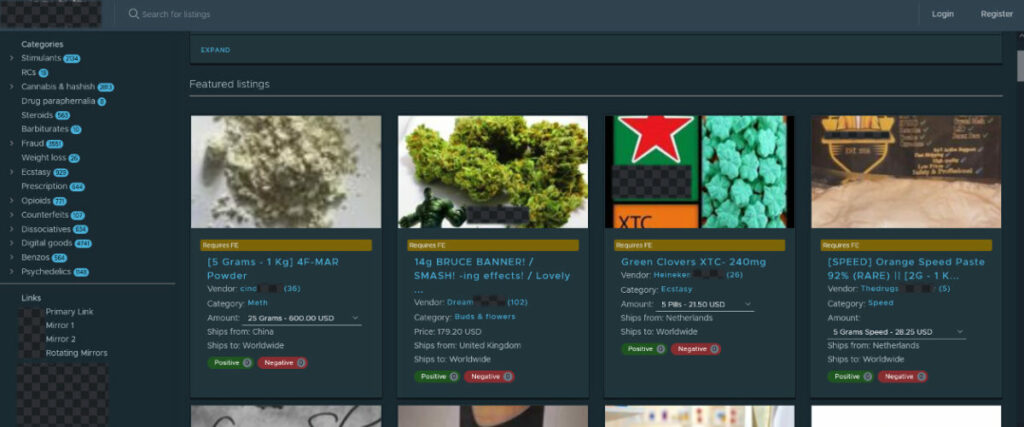
We skip giving more examples like “Hire a Hitman”, “We Hack Everyone”, “Earn 1 million in 1 month” etc., so this is enough to give you some kind of perspective what’s happening there.
Dark Web is also full of police agents doing their job, and there is a lot of examples showing “This website is sized”.
After Silkroad market, one of most popular was Alphabay. Prior to its takedown, AlphaBay reached over 200 000 users and 40 000 vendors. There were over 250 000 listings for illegal drugs and toxic chemicals on AlphaBay, and over 100 000 listings for stolen and fraudulent identification documents and access devices, counterfeit goods, malware and other computer hacking tools, firearms, and fraudulent services.
A conservative estimation of USD 1 billion was transacted in the market since its creation in 2014. Transactions were paid in Bitcoin and other cryptocurrencies. Hansa was the third largest criminal marketplace on the Dark Web, trading similarly high volumes in illicit drugs and other commodities. The two markets were created to facilitate the expansion of a major underground criminal economy, which affected the lives of thousands of people around the world and was expressly designed to frustrate the ability of law enforcement to bring offenders to justice, Europol posted in that days.
In July 2017., Two major law enforcement operations, led by the Federal Bureau of Investigation (FBI), the US Drug Enforcement Agency (DEA) and the Dutch National Police, with the support of Europol, have shut down the infrastructure of an underground criminal economy responsible for the trading of over 350 000 illicit commodities including drugs, firearms and cybercrime malware. The coordinated law enforcement action in Europe and the US ranks as one of the most sophisticated takedown operations ever seen in the fight against criminal activities online. This market was called Hansa.

Cryptocurrencies and Dark Web
In 2013, an American researcher discovered a Bitcoin-based drug market named Silk Road, which accepted only Bitcoins as payment, operated on a hidden service (that is, its site address began with http:// rather than https://), used Tor for access and relied on a PGP encryption scheme to protect users.
The same year, journalists bought heroin and cocaine from dealers in Baltimore on another market based in Tor named Atlantis.
Must Read: Legal and Illegal Uses of Cryptocurriencies
And, unlike other sites on what people increasingly call the dark web — like The Hidden Wiki — these sites have no links out to other sites or discussion boards. They are essentially dead ends: You can order drugs from them but you cannot look up where to buy them elsewhere online.
After Silk Road (which was taken down by law enforcement in 2013), bitcoin started being used as a payment method on new darknet markets.

Two main categories of cryptocurrency can be distinguished in darknet markets: privacy-oriented coins and tokens, such as monero, zcash and dash; and Bitcoin. This is due to its liquidity, ease of transfer across borders and relative anonymity compared to other cryptocurrencies.
Such currencies are referred to as privacy or mixing coins; they aim at making it hard for anyone besides those participating in transactions to link real identities with addresses.
In contrast, tokens may represent either companies’ shares or smart contracts that could be exchanged for services at a later time.
The most notorious example of using bitcoins on dark web marketplaces is probably Silk Road which saw $224 million worth of bitcoin exchanged through its marketplace from 2011 to October 2013 before it was shut down by authorities.



