In the shadows of the internet, a hidden world thrives—a clandestine realm where cybercriminals orchestrate their illicit activities, leveraging social media channels and messaging apps as their preferred platforms.
Join us on an extraordinary journey as we delve into the depths of the dark web, exposing the intricate network where data breaches, hacked logins, and nefarious dealings take place. Brace yourself for an eye-opening exploration into the underbelly of cybercrime, where anonymity reigns supreme, and the digital black market thrives.
The Dark Web’s Social Media Nexus: Unveiling a Hidden Ecosystem
Deep within the recesses of the dark web, a covert ecosystem emerges, fueled by cybercriminals seeking to exploit vulnerabilities and profit from illicit activities. As we venture into this enigmatic realm, we navigate through a labyrinth of social media channels, such as Telegram, Signal, Discord, and others, where cybercriminals converge to share stolen data, exchange hacking techniques, and collaborate on malicious endeavors. Prepare to witness the inner workings of this hidden underworld as we expose its secrets.
Within the dark web’s social media nexus, Telegram stands out as a prominent platform for cybercriminal collaboration. Its end-to-end encryption and secure messaging features make it an ideal choice for hackers seeking anonymity and a safe space to communicate. In private Telegram groups, cybercriminals converge to share valuable resources, such as data breaches, hacked logins, and compromised credentials. They exchange cutting-edge hacking techniques, discuss new vulnerabilities, and even offer their services for hire.
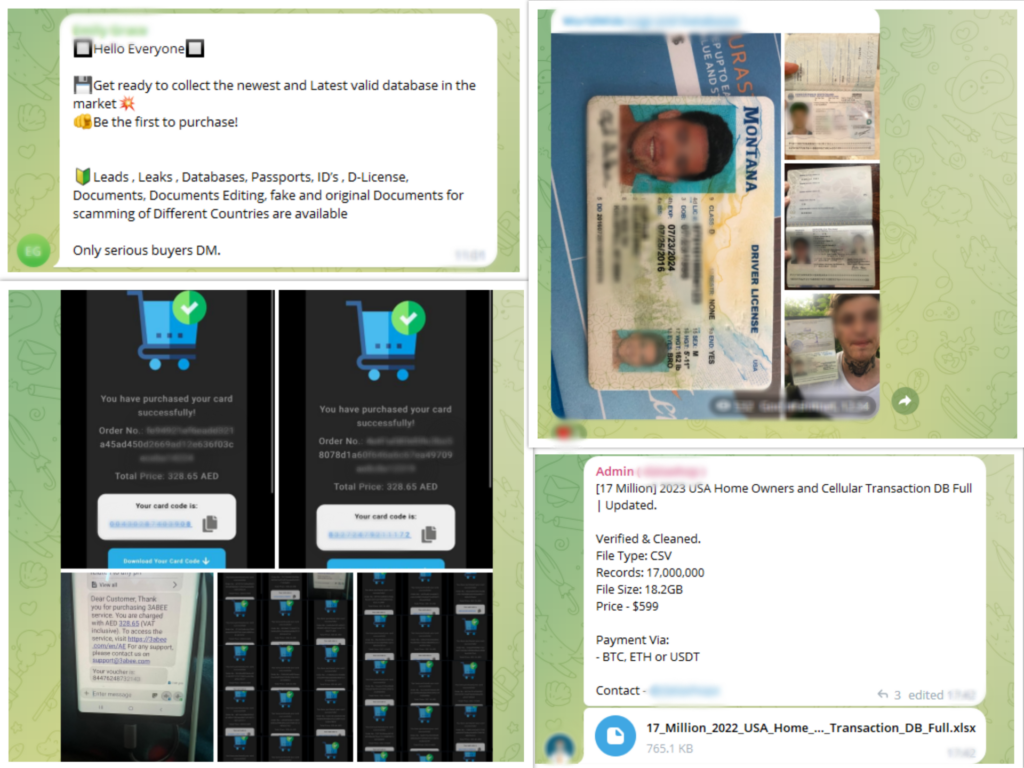
The dark web’s reliance on Telegram as a communication channel is not without reason. Its encrypted nature allows cybercriminals to share sensitive information without the fear of detection. Moreover, the platform’s user-friendly interface and vast user base make it an attractive option for criminals to connect, network, and collaborate. In these hidden corners of Telegram, one can find specialized groups dedicated to specific types of cybercrime, such as phishing, ransomware, or carding. These groups serve as knowledge-sharing hubs, where members can learn from each other, improve their skills, and access valuable resources that fuel their illicit activities.
As we dive deeper into these encrypted group chats, we uncover the inner workings of cybercriminal collaboration on Telegram. We witness the real-time exchange of hacking tips, malware distribution, and the establishment of cybercrime syndicates. The discussions range from the technical aspects of hacking to the sharing of stolen data for monetary gain. It is within these encrypted channels that cybercriminals form alliances, forge partnerships, and plan their next moves. The level of coordination and organization is both impressive and alarming, showcasing the sophistication of modern-day cybercrime.
By exposing the inner workings of the dark web’s social media nexus, we shed light on the hidden ecosystem that enables cybercriminals to thrive. It is crucial to understand the scale and complexity of these operations to combat the growing threats posed by cybercriminals. As individuals and organizations, we must remain vigilant, stay informed about the latest trends in cybercrime, and adopt robust security measures to protect ourselves from these digital menaces.
The Underground Enclaves: Exploring Dark Web Communities
Beyond Telegram, dark web denizens congregate on various other social media channels and messaging apps, creating a web of interconnected communities. These underground enclaves provide a sanctuary for cybercriminals to connect, share information, and collaborate on illicit activities. From Signal and Discord to forums and marketplaces, these platforms form the backbone of the dark web’s criminal network.
Signal, known for its robust end-to-end encryption and commitment to privacy, has gained popularity among cybercriminals seeking secure communication channels. It offers a range of features that cater to their needs, including disappearing messages, self-destructing media, and screen security. Cybercriminals utilize Signal to evade surveillance, exchange sensitive information, and discuss illicit activities away from prying eyes. The platform’s dedication to privacy makes it an attractive option for those operating within the shadows of the internet.
Discord, initially designed for gamers, has also found a place within the dark web’s underground enclaves. Its chat rooms and voice channels provide cybercriminals with a platform to gather, share knowledge, and collaborate on hacking projects. These private Discord servers serve as meeting grounds for like-minded individuals, enabling them to discuss and plan cyberattacks, share malware samples, and even offer hacking tools for sale. The relative ease of setting up and managing Discord servers has made it a favored choice among cybercriminals.
In addition to these encrypted messaging apps, dark web communities also thrive on specialized forums and marketplaces. These platforms offer a space for cybercriminals to buy and sell illegal goods and services, ranging from stolen credit card information and hacking tools to drugs and counterfeit documents. Some forums even provide tutorials, guides, and step-by-step instructions on various cybercriminal activities, catering to both novice and experienced criminals. These communities foster an environment of collaboration, where knowledge is shared, and the criminal trade flourishes.
By delving into the underground enclaves of the dark web, we expose the intricate network of platforms that facilitate cybercriminal activities. It is essential to understand the dynamics and interconnectedness of these communities to combat the ever-evolving landscape of cybercrime. Our exploration sheds light on the channels used by cybercriminals to communicate, share resources, and orchestrate attacks, equipping individuals and organizations with the knowledge needed to protect themselves in an increasingly digital world.
The Trade in Digital Shadows: Unearthing the Dark Web’s Black Market
At the heart of the dark web lies a thriving black market, where stolen data, hacking tools, and illicit services are bought and sold with virtual currencies, ensuring anonymity for both buyers and sellers. In this section, we delve into the depths of the dark web’s illicit economy, exposing the shadowy transactions and underground marketplaces that fuel cybercrime.
The dark web’s black market operates through specialized marketplaces that operate similarly to legitimate e-commerce platforms. These marketplaces, accessed through the Tor network, provide an avenue for cybercriminals to sell a range of illegal products and services. From stolen credit card details and hacked accounts to malware-as-a-service and exploit kits, these marketplaces cater to the insidious demands of cybercriminals.
One such notorious marketplace is AlphaBay, which gained infamy as one of the largest online platforms for cybercrime before its takedown by law enforcement. AlphaBay facilitated the trade in a wide array of illicit goods and services, including stolen data, drugs, weapons, and hacking tools. The marketplace operated under a system of ratings and reviews, providing a sense of trust and reliability among buyers and sellers. The closure of AlphaBay highlighted the ongoing battle between law enforcement and cybercriminals in the dark web’s black market.
Other dark web marketplaces, such as Dream Market, Wall Street Market, and Empire Market, have emerged in the wake of AlphaBay’s demise. These platforms continue to facilitate the sale of stolen data and illicit goods, albeit with varying degrees of trustworthiness and longevity. The constant cat-and-mouse game between law enforcement agencies and the operators of these marketplaces underscores the ever-shifting landscape of the dark web’s black market.
In this digital realm, cybercriminals find a thriving marketplace for their nefarious activities. The anonymity provided by virtual currencies such as Bitcoin, Monero, and Ethereum allows for secure transactions and shields the identities of those involved. The dark web’s black market has become a hub of innovation, with cybercriminals continually developing new techniques and strategies to profit from the sale of stolen information and services.
By exposing the inner workings of the dark web’s black market, we shine a light on the intricate web of criminal trade that fuels cybercrime. It is crucial for individuals, organizations, and law enforcement agencies to stay vigilant and work collaboratively to combat the illicit economy that thrives in the digital shadows. Only through awareness, education, and robust cybersecurity measures can we hope to mitigate the risks posed by the dark web’s underbelly.



